Source: Author: Datetime: 2016-01-11 Hits: 4240
On Oct. 14, 2015, the 2015 Forum on Mobile Security Technology Business Modeling was held at the Shanghai Renaissance Pudong Hotel, hosted by the SC Alliance and co-organized by mpaypass.com and Shanghai Aoh Smart Technology Co., Ltd.
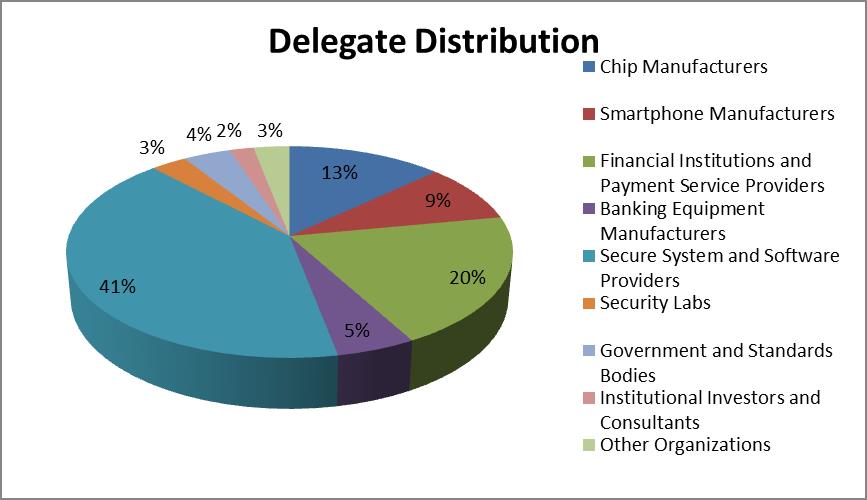
 The conference attracted nearly 250 delegates from 4 economies, including 13 chip manufactures, 9 smartphone manufactures, 20 financial institutions and payment service providers, 5 banking equipment manufacturers, 42 secure system and software providers, 3 security testing and certification labs, 4 government and standards bodies, 2 institutional investors and consultants, and 3 other organizations.
The conference attracted nearly 250 delegates from 4 economies, including 13 chip manufactures, 9 smartphone manufactures, 20 financial institutions and payment service providers, 5 banking equipment manufacturers, 42 secure system and software providers, 3 security testing and certification labs, 4 government and standards bodies, 2 institutional investors and consultants, and 3 other organizations.
• A secure smartphone needs an operating system (OS) that is part open and part closes to developers.
• The business model of security technology should take the interests of all parties into consideration. By this alone, the business model will grow faster and more sustainably.
• There is no single security technology that fixes vulnerabilities in all kinds of application scenarios. Risks must be addressed jointly by different security methods.
• Four factors must be considered for the business model of security technology: 1. Secure source;
2. Security of device personalization;
3. OS security;
4. Security management when data are migrated to a new device
• eSE has given other security technologies access to its secure communication interface. With joint efforts of other big companies, eSE will improve its feasibility in more secure application scenarios.
• HCE solution providers hope to establish long-term cooperative partnerships with their clients rather than just selling products, so they need to learn more about users’ needs in HCE.
• The low adoption rate of NFC phones is the factor that hinders the development of new mobile payment solutions like HCE.
• Users change to a new phone more and more frequently, so when they move their data to a new device, security app providers should be responsible for all the data stored in its app during and after the migration. This needs experience in security app management, so such apps cannot be managed by a single company.
• For banks, facial recognition technology has not been approved by the China Banking Regulatory Commission and Central Bank, but fingerprints can still be used in the banks' payment app, though it is not requested when a client opens a new account. Some companies are using fingerprints, but not extensively enough to be applied on a large scale.
• In Korea, it is not certain whether binding a physical card is needed for the creation of HCE virtual cards, but it is said that one physical card can bind multiple virtual cards.
• Regarded as the most secure technology, eSE is cooperating with other convenient secure authentication methods in a hope to provide a convenient user experience without compromising on security.
• The current dual-OS solution for secure smartphone is not mature, and some apps are not compatible with both systems.
• Chinese OS developers will enjoy an advantage in expanding the domestic market in future.
• The reason why some main Chinese smartphone manufacturers have not given up NFC phones is that many NFC-enabled apps provide a good user experience. Though such apps have a lot of problems, they are not facing technical issues. The problem lies in a conflict of interest among stakeholders. Some phone manufacturers are willing to break the ice by lowering their thresholds and working with both upstream and downstream companies in order to provide better user experience.
• Biometrics gives people real convenience but its security issue is like a double-edged sword. Because of the uniqueness of biometric information, a large number of personal information is being sold and abused. How to manage and protect users’ biometric information poses a major challenge to the biometric industry.
• Seeing a booming smart device market, many startups work really hard in this sector, investing a lot of time and effort to develop solutions in hopes to realize their dreams of entrepreneurship. Faced with the risk of pirates, they have to expand their market discreetly. However, their products might lose the advantage of perfect timing to enter this ever-changing market of fleeting business opportunities. To alleviate manufactures’ concerns, a security chip designed with an anti-pirating feature has been launched and used widely, paving the way for the marketing of smart devices.
• The current method for online identification is to use a significant amount of personal information to prove you are indeed yourself, which brings about the risk of large-scale privacy leakage.
• The current biometric identification technology cannot promise a100 percent match rate, but cryptology is confidential, integrated and undeniable.
• There are three factors in cryptology used to prove your identity: what you are, what proof you have, and what you know, which is quite subjective.
In a Nutshell
Security appears to be a technology term, but it is a managerial problem when being used in real scenarios and business models. A lot of technology experts and knowledgeable practitioners can solve a technological problem, but it doesn't mean it can be perfectly adapted to a business model. Hitech criminals are not ordinary people. If you lock your bike, they are still able to steal the whole locked bike. When a problem occurs, the most difficult part does not lie in technology but rather in the intricate relationship of stakeholders.
As everyone thinks from different perspectives, they give different solutions to the same problem. Some company promises that if you dare to pay, we dare to indemnify. However, some large- and high-leveled institutions trusted by consumers cannot solve the problem in such a popular way, because they are restricted by the financial system.
We all know it's better late than never. Even if we lock the barn door after the horse is stolen, we can still prevent losing the rest. But the reality is that compared with the profit of selling the rest of the horses, many companies don't care about the loss of a single horse. They choose to do nothing until something really bad happens.
So, let’s ask ourselves the following questions: How much is the cost of insecurity? Who should pay for insecurity? If a problem occurs, will we simply lose one horse?
For more information, please contact Secretary General of SCA Neil Ding
Tel: 186 2161 0833
Email:neil.ding@smart-alliance.com
This article is written by SCA. You are welcome to use it, but please indicate its source.


At the conference, security experts from 9 organizations analyzed the latest developments in mobile security technology and proposed business models regarding both upstream and downstream developmental demands in the industry.

• A secure smartphone needs an operating system (OS) that is part open and part closes to developers.
• The business model of security technology should take the interests of all parties into consideration. By this alone, the business model will grow faster and more sustainably.
• There is no single security technology that fixes vulnerabilities in all kinds of application scenarios. Risks must be addressed jointly by different security methods.
• Four factors must be considered for the business model of security technology: 1. Secure source;
2. Security of device personalization;
3. OS security;
4. Security management when data are migrated to a new device
• eSE has given other security technologies access to its secure communication interface. With joint efforts of other big companies, eSE will improve its feasibility in more secure application scenarios.
• HCE solution providers hope to establish long-term cooperative partnerships with their clients rather than just selling products, so they need to learn more about users’ needs in HCE.
• The low adoption rate of NFC phones is the factor that hinders the development of new mobile payment solutions like HCE.
• Users change to a new phone more and more frequently, so when they move their data to a new device, security app providers should be responsible for all the data stored in its app during and after the migration. This needs experience in security app management, so such apps cannot be managed by a single company.
• For banks, facial recognition technology has not been approved by the China Banking Regulatory Commission and Central Bank, but fingerprints can still be used in the banks' payment app, though it is not requested when a client opens a new account. Some companies are using fingerprints, but not extensively enough to be applied on a large scale.
• In Korea, it is not certain whether binding a physical card is needed for the creation of HCE virtual cards, but it is said that one physical card can bind multiple virtual cards.
• Regarded as the most secure technology, eSE is cooperating with other convenient secure authentication methods in a hope to provide a convenient user experience without compromising on security.
• The current dual-OS solution for secure smartphone is not mature, and some apps are not compatible with both systems.
• Chinese OS developers will enjoy an advantage in expanding the domestic market in future.
• The reason why some main Chinese smartphone manufacturers have not given up NFC phones is that many NFC-enabled apps provide a good user experience. Though such apps have a lot of problems, they are not facing technical issues. The problem lies in a conflict of interest among stakeholders. Some phone manufacturers are willing to break the ice by lowering their thresholds and working with both upstream and downstream companies in order to provide better user experience.
• Biometrics gives people real convenience but its security issue is like a double-edged sword. Because of the uniqueness of biometric information, a large number of personal information is being sold and abused. How to manage and protect users’ biometric information poses a major challenge to the biometric industry.
• Seeing a booming smart device market, many startups work really hard in this sector, investing a lot of time and effort to develop solutions in hopes to realize their dreams of entrepreneurship. Faced with the risk of pirates, they have to expand their market discreetly. However, their products might lose the advantage of perfect timing to enter this ever-changing market of fleeting business opportunities. To alleviate manufactures’ concerns, a security chip designed with an anti-pirating feature has been launched and used widely, paving the way for the marketing of smart devices.
• The current method for online identification is to use a significant amount of personal information to prove you are indeed yourself, which brings about the risk of large-scale privacy leakage.
• The current biometric identification technology cannot promise a100 percent match rate, but cryptology is confidential, integrated and undeniable.
• There are three factors in cryptology used to prove your identity: what you are, what proof you have, and what you know, which is quite subjective.
In a Nutshell
Security appears to be a technology term, but it is a managerial problem when being used in real scenarios and business models. A lot of technology experts and knowledgeable practitioners can solve a technological problem, but it doesn't mean it can be perfectly adapted to a business model. Hitech criminals are not ordinary people. If you lock your bike, they are still able to steal the whole locked bike. When a problem occurs, the most difficult part does not lie in technology but rather in the intricate relationship of stakeholders.
As everyone thinks from different perspectives, they give different solutions to the same problem. Some company promises that if you dare to pay, we dare to indemnify. However, some large- and high-leveled institutions trusted by consumers cannot solve the problem in such a popular way, because they are restricted by the financial system.
We all know it's better late than never. Even if we lock the barn door after the horse is stolen, we can still prevent losing the rest. But the reality is that compared with the profit of selling the rest of the horses, many companies don't care about the loss of a single horse. They choose to do nothing until something really bad happens.
So, let’s ask ourselves the following questions: How much is the cost of insecurity? Who should pay for insecurity? If a problem occurs, will we simply lose one horse?
For more information, please contact Secretary General of SCA Neil Ding
Tel: 186 2161 0833
Email:neil.ding@smart-alliance.com
This article is written by SCA. You are welcome to use it, but please indicate its source.
